
Most Common RAID Failures And Data Recovery Insights
The use of RAID (Redundant Array of Independent Disks) configurations is common in large corporations. In fact, the way in which this system works has increased the popularity of it being used in small and medium-sized businesses as well. Essentially, RAID is a method of accessing multiple individual disks in a set-up that acts as […]
Continue Reading
How to Protect Your Website From Hackers Via The .htaccess File And How to Increase Your Web Data Security
Hackers are without a doubt annoying, to say the least. They tend to put their noses anywhere they want, provided they see the potential of getting something out of it. If you are concerned about your data, all you really need to do is make off-site backups of your webserver and crank up your security […]
Continue Reading
Monolithic SD Cards Pinout – Data Recovery Is Possible On Monolithic Devices
Is data recovery possible from monolithic devices? Well, if you listen to many industry professionals who work in the data recovery industry, apparently not. Sure, in many cases that is a fact. However, there are some, where data can be recovered using Pinout technology. You had to already have expected me to say that, didn’t […]
Continue Reading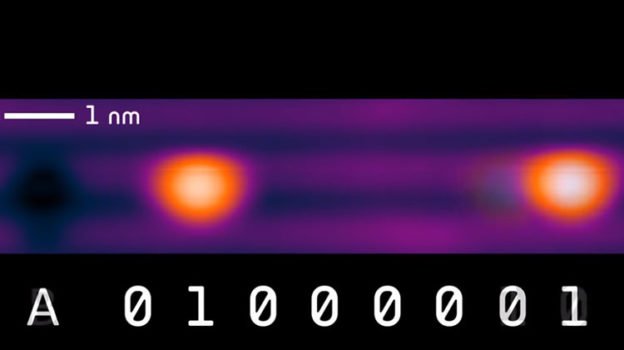
Canada Staying Ahead With Storage Memory Development. New Super Dense And High Capacity Storage. How Soon Will It Go Public?
For some reason, you don’t normally hear or see news about the technology sector or industry advancements in Canada. However, an Alberta-based Ph.D. student has something that is truly newsworthy. Originally shared by GlobalNews, Roshan Achal has developed a new storage memory that could exceed the capabilities of current hard drives by one-thousand times. Thanks […]
Continue Reading
Cyber Criminals Are Getting Highly Creative & Sophisticated. MacGyver would be proud.
It’s a fact. Cybercriminals are most definitely keeping up with the times. Ransomware is a fine example of this. It can infect your computer in many different ways. You can open an attachment from what looks like a legitimate website and end up launching a malware program that will run underneath your current operation and […]
Continue Reading « Previous Page — Next Page »