
Today’s digital world is a very dangerous place if you don’t take the proper precautions to protect yourself, your computers and your Wifi access. That’s correct, your Wifi system has to be secure to prevent hackers from abusing more than your data limits. Hackers can use your unprotected WiFi signal to get into your network and then into your connected devices. Once there, your data – including personal information – can be stolen.
There have been several different types of WiFi security protocols developed and each has advantages and disadvantages. If you are not sure what you are looking for, the letters used to identify each may seem a bit on the confusing side. For example, if you don’t know what WPA or WEP stand for, you might have trouble finding the right security solution for your wireless connections.
If you are looking to protect your WiFi access by restricting who can use it, your best defense is to set the security protocol to WPA2. In this article I will break each of the wireless protocols down for you and tell you if they can be hacked or not
Here’s a look at the three different types of WiFi protocols and what they can and cannot do to protect your connected devices.

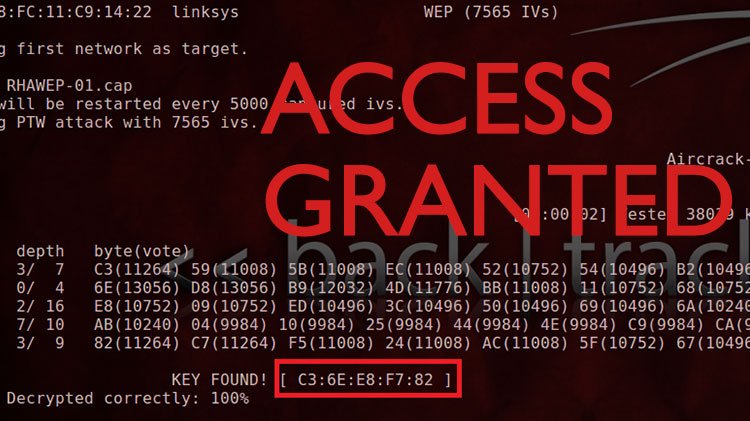
1. WEP – Wired Equivalent Privacy
This is the protocol that was first developed in the late 1990s. It was meant to protect wireless connections from hackers and uses 64 bit to 128 bit encryption. For the time they first were available, they provided a fairly safe environment for wireless users. However, in today’s market, WEP can easily be hacked with BackTrack Linux.
2. WPA-PSK – WiFi Protected Access
This ‘updated’ protocol was developed shortly after WEP became prone to hackers. It uses 256 bit encryption without AES (Advanced Encryption Standard). Although WPA-PSK is extremely hard to breach, it is still vulnerable to hacking.
3. WPA2-PSK – WiFi Protected Access 2
This is actually an update to the WPA algorithm which added the AES (Advanced Encryption Standard). This happens to be the very same standard in use by Bitcoin to encrypt their crypto currency wallets. It is bullet proof and un-crackable simply because of the AES based encryption.
In Review
So, WEP is the bottom of the totem pole as it can be hacked by just about anyone who will want to follow some simple to moderate steps online. The interesting thing is, there are several tutorials and step-by-step guides available so if you ever wanted to crack your neighbors WiFi and borrow their signal, you could easily do that, which I don’t recommend as you would be literally invading privacy and breaking the law – which is an offense (It’s an offense in the Canadian Criminal Code (section 326) punishable by up to 2 years in jail and $5000 fine per occurrence). In fact, it’s not nearly as difficult to do as you may think. You will need some specific tools such as a network card or WiFi adapter that has packet injecting capabilities. There is a comprehensive tutorial in case you decide to try and test your own security environment.
WPA is a little harder to crack. That’s because it uses a 256 bit encryption algorithm, but even with this type of security protocol, a very skilled hacker would be able to penetrate your connection.
Hacking is virtually impossible with WPA2 as it uses AES algorithms and that happens to be the same as BitCoin so you know this is going to be a very well protected WiFi access point. We are not aware of any successful penetrations with WPA2, although there are sources online stating that this has happened. To date, I have yet to have seen a truly cracked WPA2 security protocol.
If you use the internet daily with wireless access, it is important to keep your data and online use as safe as possible. One of the best ways to do this is to keep your WiFi connection secure. You never know who may be trying to hack into your signal and for what reason. For some hackers, cracking your WiFi to get to your data is the quickest and easiest path they can follow. So, to keep them out, be sure to use WiFi connection gear that has WPA2 security protocols in place.

