
It’s a fact. Cybercriminals are most definitely keeping up with the times. Ransomware is a fine example of this. It can infect your computer in many different ways. You can open an attachment from what looks like a legitimate website and end up launching a malware program that will run underneath your current operation and you don’t know what happened until it’s too late.
You can also get infected by falling for what sounds like a legitimate request through a phone call. You could be asked to download a form from what appears to be the CRA website and end up infecting your computer with malware that steals your credit card information. Sometimes the cybercriminals have little time once they seize your credit card number and turn around to sell it on Darknet websites for some Bitcoin and whoever ends up with your number can do what they wish with it.
Here’s an interesting twist to the whole situation. There are even times when the actual companies involved become the Bad Guys. There was a story of a company based in the United Kingdom that went ahead and hired hackers to do the dirty work for them. The end result in this particular story was that a total of 650,000 Bitcoins were stolen from a French cryptocurrency exchange operation and then laundered.

The question that comes to mind is, was the company actually behind it or did hackers end up using the company as a front to remain immune? That is just an example of how sophisticated cybercriminals have become. They are the robbers and thieves of the new technological world we live in and it also means we all have to work a little harder in order to keep our information – the data we store on our electronic wifi-enabled devices – secure.
Hackers are finding ways to hack into personal computers and installing hidden mining software and using those computers as mining rigs – or as horsepower – to mine cryptocurrency. Cryptocurrency mining takes a toll on computer systems that are built just for that purpose. These hackers have found a way around the cost and labor of building their own mining rigs by piggybacking on yours – with you paying for the power used to mine.
Here is another hijacking technique.
Hackers who manage to find vulnerabilities in large corporate servers or CRM applications – which normally handle hundreds of customer’s credit card data, will steal it. But then they will turn around and sell that credit card information in bulk on the Darknet. Those companies are the big losers as a result as their customers will leave based on the lack of security when credit card data gets stolen. You can’t really blame the customers who likely feel stung by the company they trusted with their information. For example, if it turns out that the exact file that your hacker is looking for just happens to be hidden in a place where it was untouched by the scratches then guess what? Your data is ripe for the picking. Well, at least whatever is in that particular undamaged file. That is usually enough to provide a hacker with something to exploit or turn into instant cryptocurrency through a fast flip on the Darknet.
But it gets even more sophisticated.
Cybercriminals have gotten to the point where they are now able to steal AES keys. These keys are used to keep cryptocurrency wallets secure such as with Bitcoin. It may have sounded impossible to do as recent as last week, but it is happening.
Security experts at Fox-IT have actually been able to demonstrate the possibility. What happens is that cyber thieves have devised a way in which they can ‘sniff’ AES-256 bit encryption keys from a distance of a meter (3.3-feet).
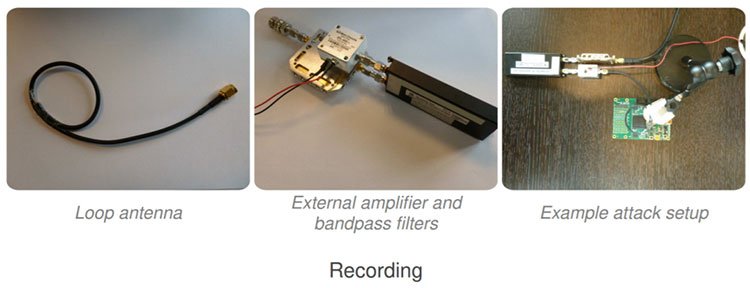
Image Source: https://securityaffairs.co/wordpress/60383/breaking-news/aes-256-side-channel-attack.html
The scary thing is, that in this particular case, a tool basically thrown together with various computer parts you can easily get at your local electronics store does the job. It ‘sniffs’ at the electromagnetic signal that is generated by the computer. It’ll take five minutes to complete the job from a meter but when closer – 30-centimetres (11.8-inches) it takes less than a minute to grab an AES key.
“MacGyver would be proud.“
Hacking has moved far beyond the days where computer operators were just goofing around to see if they could access any unauthorized files. Hacking has become a powerful tool for criminals who choose to break into data banks and steal whatever they want knowing that there is someone on the Darknet willing to buy that information.

It is actually fair to say that hacking has become a science that has kept software developers working overtime in their quest for programs that are secure and safe to use. But the reality is, when the information superhighway first opened, it became a whole new route for the real Bad Guys to travel.
New technology created new ways in which we communicate, shop and gather information. It also presented an attractive way to attack and steal information from others. The science of hacking is always evolving with new ways to steal and exploit users being created on a daily basis. Even if you do not feel that you have anything of worth to a cybercriminal, you can still become a victim just by using the internet.

